iVALT Identity Validation Platform®
A single, unified platform for validating the identity of humans, IoT devices, and AI agents.
Human Authentication: Mobile-Centric
No usernames/passwords — mobile number as secure ID
Multi-Factor (up to 25) Authentication:
Biometrics: Face, fingerprint
Device identity: Registered phone
GPS & Time: Real-world context
Dynamic Variables: Real-time random data (weather, stocks, etc.)
AI-driven factor selection
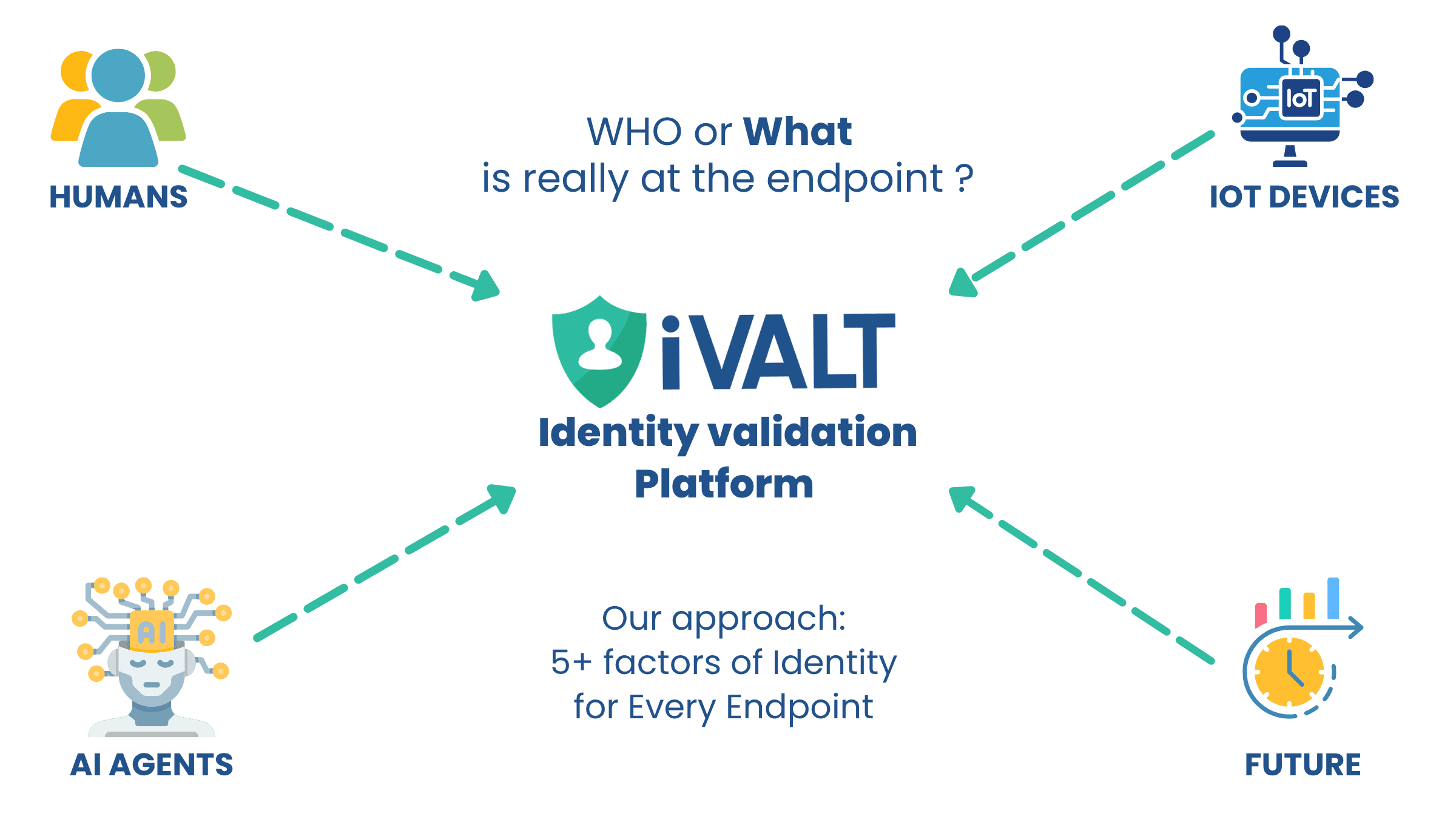
Next Gen MFA for Everything
Result: Dynamic, context-aware authentication that is nearly impossible to hack, even by AI.

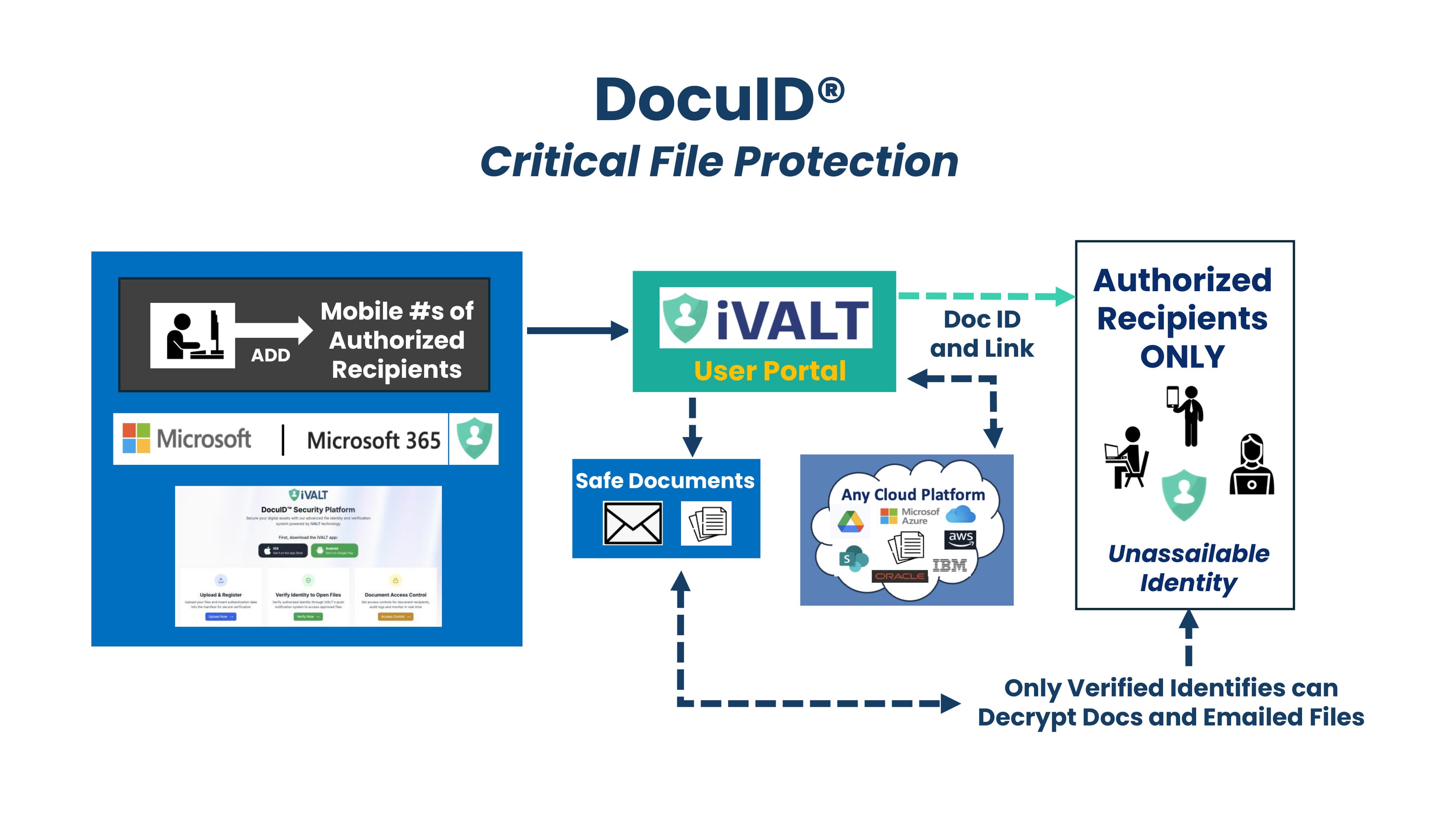
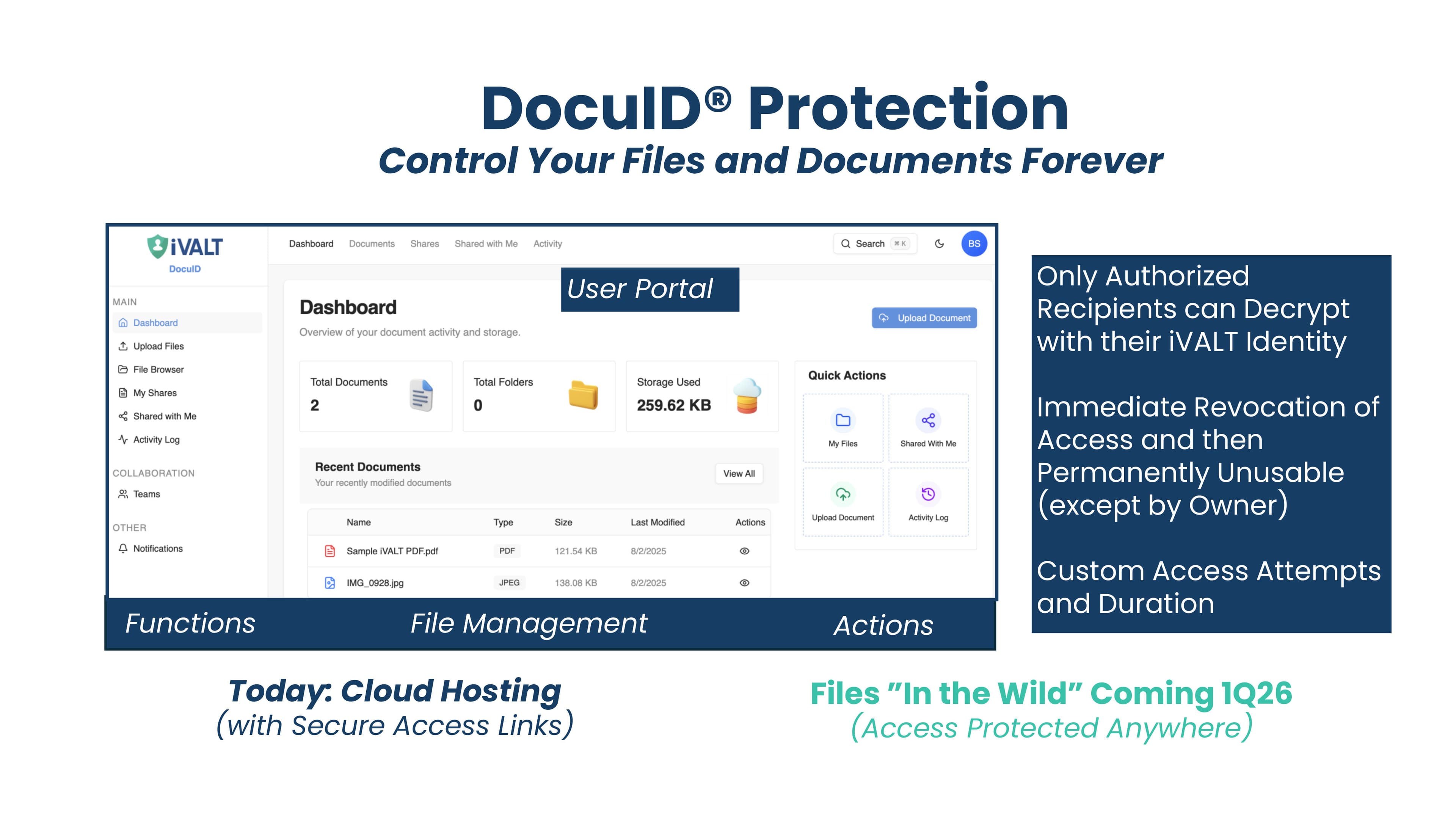
Stop Data Exfiltration
Generative AI and DocuID® Data File Security
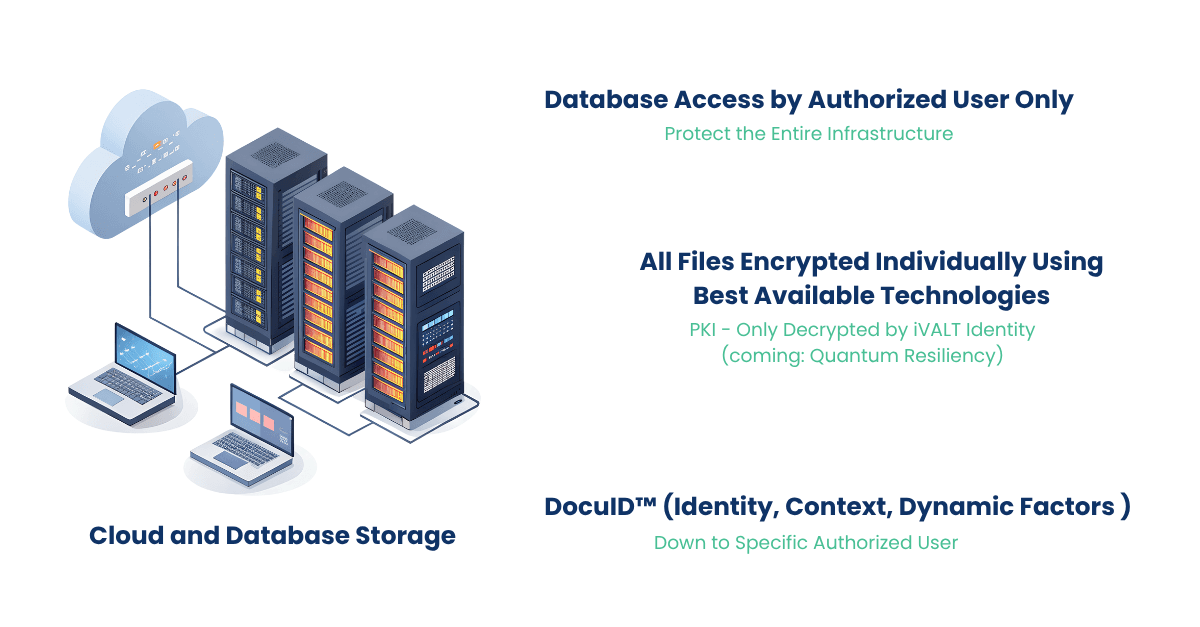
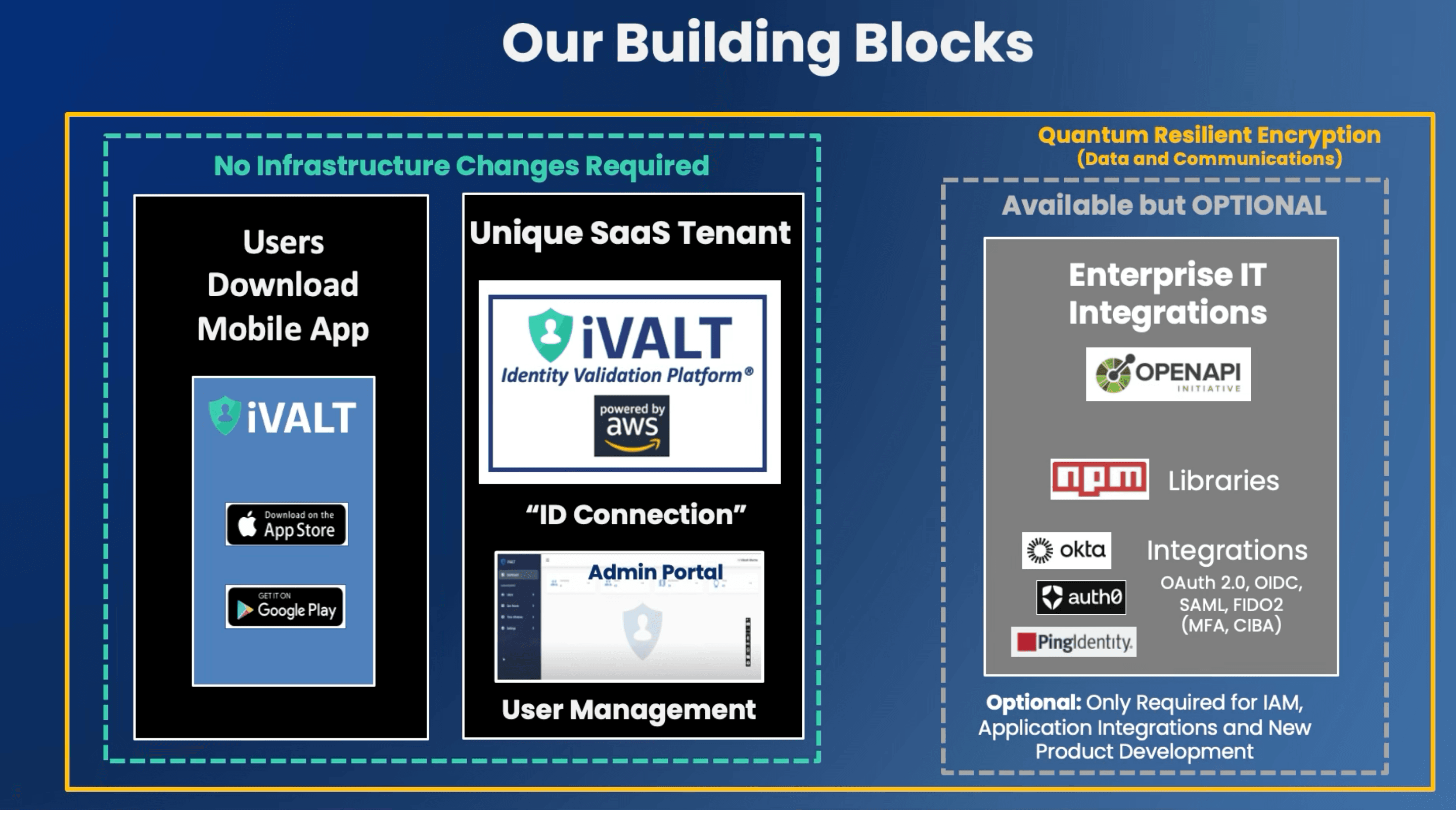
Solution Components
Easy Deployments. Fast User Onboarding. User Management.