Why iVALT ?

Pioneering the Future of Identity
Understanding the needs of the market and creating solutions that are future-proof.
Using the:
Best Available Technologies Widely available at Any Point in Time
A Platform Approach to Enable Customization for the Unique Needs of Customers
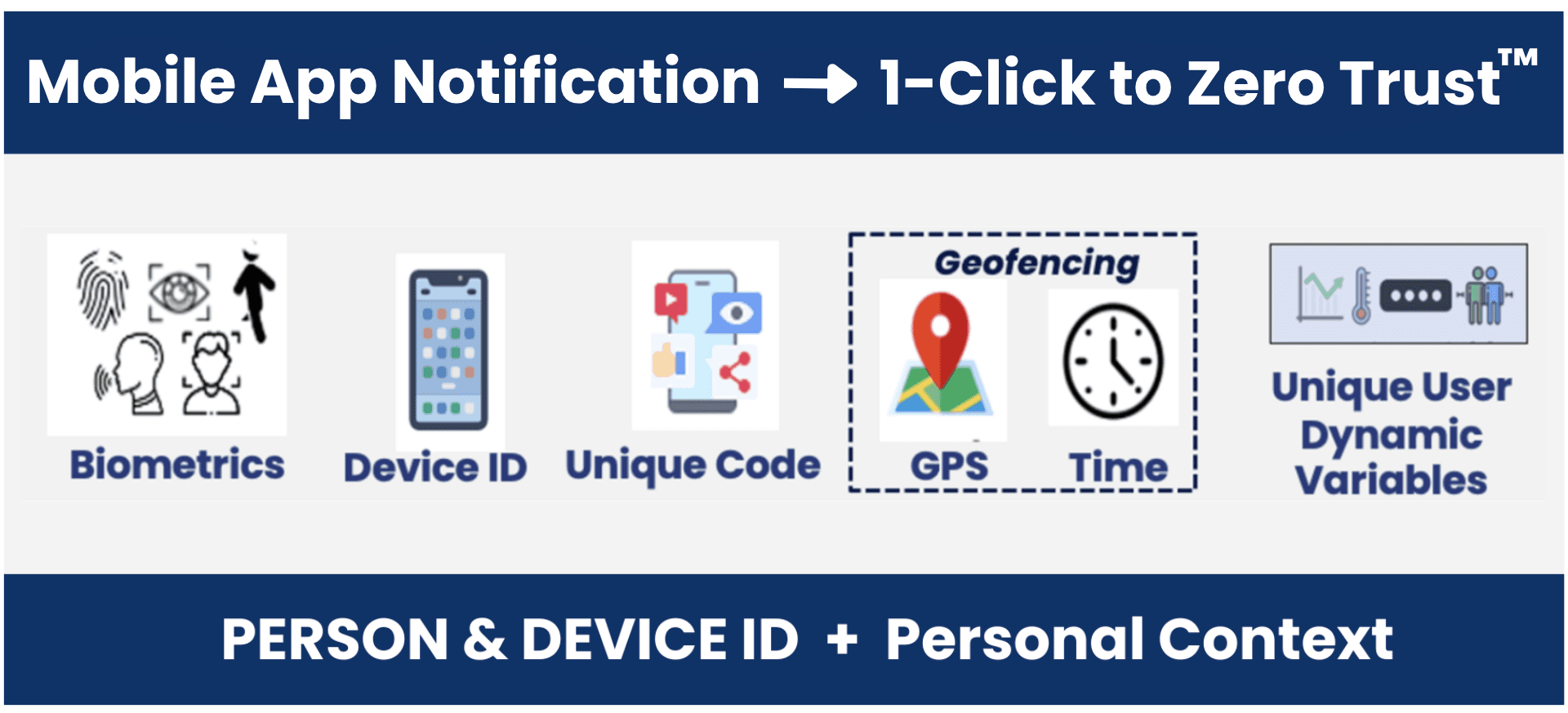
Biometrics and Device ID PLUS Contextual Factors and Dynamic Variables to Enable Definitive Identity Anywhere and for Any Application
Control of their Identity goes back into the Hands of Individuals
A 1-Click User Experience for All Use Cases
Our Approach is “Next Generation MFA” without Credentials
Up to 25+ Factors
1-Click UX
Backward Compatible
The Game Changing Approach to Security
Stolen Credentials become worthless
Fake communication are stopped
User Can Control their Context to Set Geofencing and Time Factors
Definitive Identity Verification
Enterprise Apps
IAM (CIBA)
Physical Access
In-Person ID
Communications
Documents Control
Many Others
Benefits We Bring to a Partnership
Transform your business with our comprehensive identity validation platform that delivers measurable value across multiple dimensions.
Fraud Reduction
Across the Board
Comprehensive security through multiple authentication factors that make stolen credentials worthless.
Biometric authentication with face and fingerprint recognition
25+ security factors for maximum protection
Real-time verification and threat detection
Frictionless UX
User Experience
Simplified authentication process that enhances user satisfaction while maintaining security.
1-Click authentication
No passwords or complex procedures required
Seamless integration
New Revenue Opportunities
Business Growth
Unlock new revenue streams with premium identity services and advanced security solutions.
Premium Identity-as-a-Service offerings
Advanced Document Security solutions
All Key Use Cases
Comprehensive Coverage
Support for all critical business operations and customer interaction workflows.
Alert responses
User actions
Customer service
Data access
Simple Business Model
Transparent Pricing
Straightforward pricing structure that makes budgeting and scaling predictable.
Per user per month transparent pricing
No hidden fees or complex licensing
Scalable plans for businesses of all sizes
Constant Optimization
AI-Driven Enhancement
Continuous improvement through machine learning algorithms that adapt to your business needs.
Per use case optimization and customization
AI/ML models that learn and improve over time
7 Patents Granted, 10+ Patents Pending, 4 Registered Trademarks
iVALT is a leader in the field of identity verification, with a strong portfolio of patents and trademarks.